



The average time to detect a cyber breach is 280 days.
0
Days
Every 39 seconds, a security attack is carried out by a hacker.
0
Seconds
The global cost of cybercrime is projected to reach $10.5 trillion annually by 2025.
$
0
Trillion
43% of security attacks target small-scale businesses.
0
%
Over 90% of cyberattacks originate from phishing emails.
0
%
The average time to detect a cyber breach is 280 days.
0
Days
Every 39 seconds, a security attack is carried out by a hacker.
0
Seconds
The global cost of cybercrime is projected to reach $10.5 trillion annually by 2025.
$
0
Trillion
Mobile devices became a target,
with over 90% of mobile malware
delivered via email.
with over 90% of mobile malware
delivered via email.
0
%
Small businesses are targeted
in 43% of cyberattacks.
in 43% of cyberattacks.
0
%
Over 90% of cyberattacks start
with a phishing email.
with a phishing email.
0
%
We Secure Your Digital Footprint
- Security Consulting Services
- Technology Integration Services
- Managed Security Services
Consulting Services
Our cybersecurity consulting services focus on strengthening your cyber resilience and enhancing cyber defense readiness to help you stay protected against future security threats, regardless of the industry vertical or geographic region in which you operate. We aim to align your cybersecurity strategies and technology landscape with your established business imperatives.

- Compliance Readiness
- Risk Assessment
- Breach Assessment
- Cloud Security
- Strategic Advisory
Technology Integration Services
The solutions we provide for technology integration in cybersecurity are designed to bridge gaps in your business’s cybersecurity roadmap and ensure protection against cyber threats. From network security to core applications, our experts with extensive cybersecurity expertise work closely with you to develop and execute a customized integration and implementation strategy that reinforces your cybersecurity posture.

- Endpoint Security
- Application Security
- Zero Trust Network Access
- Network & Cloud Security
- Identity & Access Control Management
Managed Security Services
Our Managed Security Services ensure continuous monitoring of your cybersecurity operations, defense readiness and incident response 24/7 to help you stay ahead and protected against complex threats. By entrusting these critical functions to a managed security services provider like us, you can fully focus on your core business objectives while your digital assets are safeguarded by our cybersecurity experts against potential cyber threats.

- Managed Security Operation
- Vulnerability Management
- Managed Application Security
We Ensure the Protection of
Business Vitals from Cyber Threats
We provide customized cybersecurity services for different industry verticals, ranging from small businesses to large corporations.
Our comprehensive cybersecurity expertise covers the entire landscape, mitigating a variety of cyber threats.
Government & Federal Agencies
Government and federal agencies oversee vast amounts of highly sensitive data, ranging from individuals’ passport information and social care records to confidential military documents. In today’s demanding environment, which is increasingly vulnerable to cyber threats, it is of utmost importance to have a resilient cybersecurity system in place to mitigate security attacks, reduce damage, and ensure prompt mission continuity.
Healthcare
The healthcare sector has undergone a significant shift in its digital landscape in recent years, making cybersecurity a critical necessity for protecting valuable insights, sensitive healthcare information, and patients’ personal data.
BFSI & NBFC
The potential security attack surface for banks has increased significantly due to their ever-evolving digital footprint. Cyber breaches can lead to financial losses, operational disruptions, reputational harm, and broken customer trust due to perceived betrayal.
Manufacturing
The global manufacturing industry has recently become the center of attention, targeted by organized security attacks. This has resulted in substantial business revenue loss and deterioration of brand image, and has further caused interrupted supply chains, ecosystem damage to affiliated businesses, and massive job losses.
Information Technology
The rapid adoption of secure cloud technologies like multi-cloud and hybrid cloud, IoT and OT integration, and the growing gap in skilled professionals with cybersecurity expertise are propelling IT businesses globally towards rising cyber risks. The impact of a cyber breach could have long-lasting effects in a globally competitive market space.
Others
Across industries, cybersecurity challenges are growing at a rapid pace, resulting in significant and often unrecoverable financial losses, posing a severe threat to brand reputation, and disrupting business operations from achieving their regular goals. Businesses are striving to formulate robust cybersecurity strategies that align with their organizational objectives.
Technology Integration Services
Our Professional Services team are here to guide you to keep up with industry best practices and maximise your return on investment on your security journey.
- Endpoint Security
- Network & Cloud Security
- Network & Cloud Security

Our Structured Approach to Service Engagements
(Consult – Design – Deploy – Operate – Transform Value Chain)

Gathering Business Insights
Gather the client’s organizational needs, technologies and software, professionals, procedures, data, and success criteria metrics.

Cybersecurity Architecture
Design a robust cybersecurity architecture to enhance short-term resilience against cyber threats and seamlessly support future business development.

Structured Implementation
Execute on-time project delivery within a cost-effective budget and according to the defined scope by adopting structured implementation, continuous monitoring, and comprehensive planning methodologies that align with the business’s objectives.
Project Deliverable Closure
Finalized approval of critical organizational deliverables through real-time testing of project success criteria, integration of technologies and software, and strict adherence to established cybersecurity operations standards and compliance requirements.

Project Documentation
Extensive documentation of the technological architecture, service workflow procedures, and project governance strategy, including KPIs and other metrics for productive project monitoring.
Continuous Optimization
Persistent improvement of cybersecurity architecture, service workflows, project governance, and SLAs/metrics to stay updated with cyber threats that are rapidly evolving in complexity.
Gap Assessment (Marketing/Campaign)
Get the insights you need to make strategic decisions for your business.
A GAP Analysis can help you see the big picture and identify your priorities.
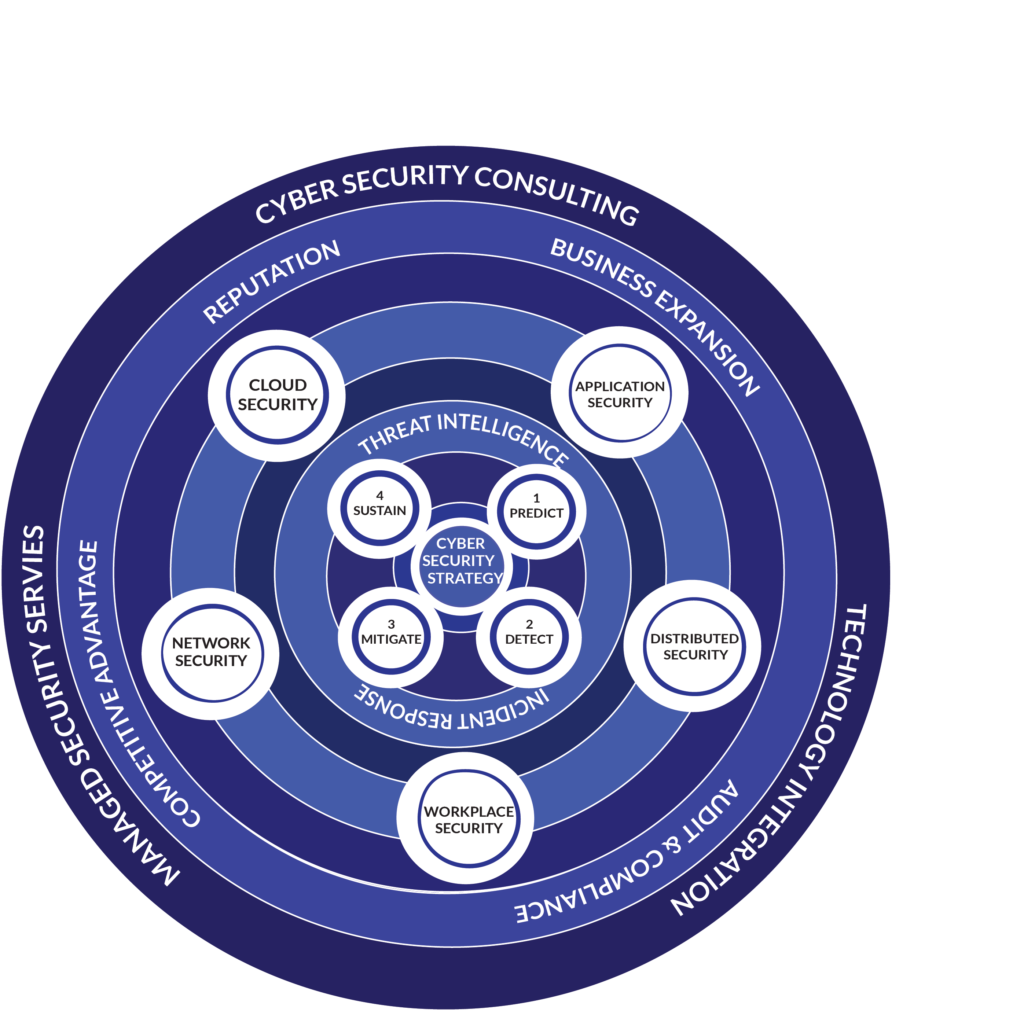
With Us, You Are Investing in Both the Tangible & the Intangible
We offer end-to-end protection for your establishment’s digital assets, mitigating cyber risks and minimizing the impact of evolving and complex cyber threats. Additionally, we nurture a culture of cybersecurity within the establishment by ensuring awareness amongst employees of industry best practices and by enforcing effective security policies, strategies, and technologies.
- Build secure business operations and continuous delivery.
- Cyber hygiene culture through Employee Awareness.
Gap Assessment
Get the insights you need to make strategic decisions for your business.
A GAP Analysis can help you see the big picture and identify your priorities.
A GAP Analysis can help you see the big picture and identify your priorities.
Gap Assessment
Get the insights you need to make strategic decisions for your business.
A GAP Analysis can help you see the big picture and identify your priorities.


Neutralize the Cyber Threats Before They Reach You !
Acquire a rapid report of your company’s cyber risk profile. Identify compromised credentials, code leaks, exposed classified files, fake domains, rogue applications, misconfigured cloud storage and more that endanger your business’s cybersecurity posture.
Building a Secure Future Together
Experience the difference Secureinteli brings with its unmatched cybersecurity expertise, and empower your organization to achieve greatness.
Assets Protected
0
k+
Risk Reduction
0
%

A few words from our users

“I've worked with Secureinteli for over a year. They're great - always available for security issues and provide peace of mind. Highly recommended!”
Alexa Jones
@therealalexjones

“Cyber Security essential for our success. Their expertise & support keep us secure. Advising us to make our data security the top priority.”
Edward Snowden
@snowden

Create this account for myself secuse in the future. best site to earn.
Jenny
Co-Founder
Brands That Trust Secureinteli
Got any questions?
Got any questions? Our knowledgeable team is here to answer any questions you may have about our services. Please feel free to contact us if you need help with anything.
What can I do to protect myself from cyber threats?
At Secureinteli, our top priority is protecting our clients from cyber threats. The best way to protect yourself is to keep your systems up-to-date with the latest software, use strong passwords, and configure all of your settings to the highest security level. Additionally, look out for suspicious emails and avoid clicking links from unknown sources. Finally, make sure to regularly backup your data in case of a cyber attack.
What cyber security services does your company provide?
At Secureinteli, our top priority is protecting our clients from cyber threats. The best way to protect yourself is to keep your systems up-to-date with the latest software, use strong passwords, and configure all of your settings to the highest security level. Additionally, look out for suspicious emails and avoid clicking links from unknown sources. Finally, make sure to regularly backup your data in case of a cyber attack.
How to secure my data & devices?
At Secureinteli, our top priority is protecting our clients from cyber threats. The best way to protect yourself is to keep your systems up-to-date with the latest software, use strong passwords, and configure all of your settings to the highest security level. Additionally, look out for suspicious emails and avoid clicking links from unknown sources. Finally, make sure to regularly backup your data in case of a cyber attack.
How protect you from cyber attacks?
At Secureinteli, our top priority is protecting our clients from cyber threats. The best way to protect yourself is to keep your systems up-to-date with the latest software, use strong passwords, and configure all of your settings to the highest security level. Additionally, look out for suspicious emails and avoid clicking links from unknown sources. Finally, make sure to regularly backup your data in case of a cyber attack.
Join our newsletter
Stay up to date on Secureinteli’s cureated feed of the latest cyber security news, trends, and tips by joining our newsletter!
































