- Home
- Technology Integration Services
Technology Integration
At Secureinteli, we approach IT security with a “Rules Before Tools” philosophy. We first assess benchmarking industry-leading cyber security resilience frameworks such as NIST-CSF and then architect and implement tailored technology controls that align with your business and provide deep visibility, detection, and response capabilities, helping defend your network against sophisticated cyber threats and maintain a robust security posture.
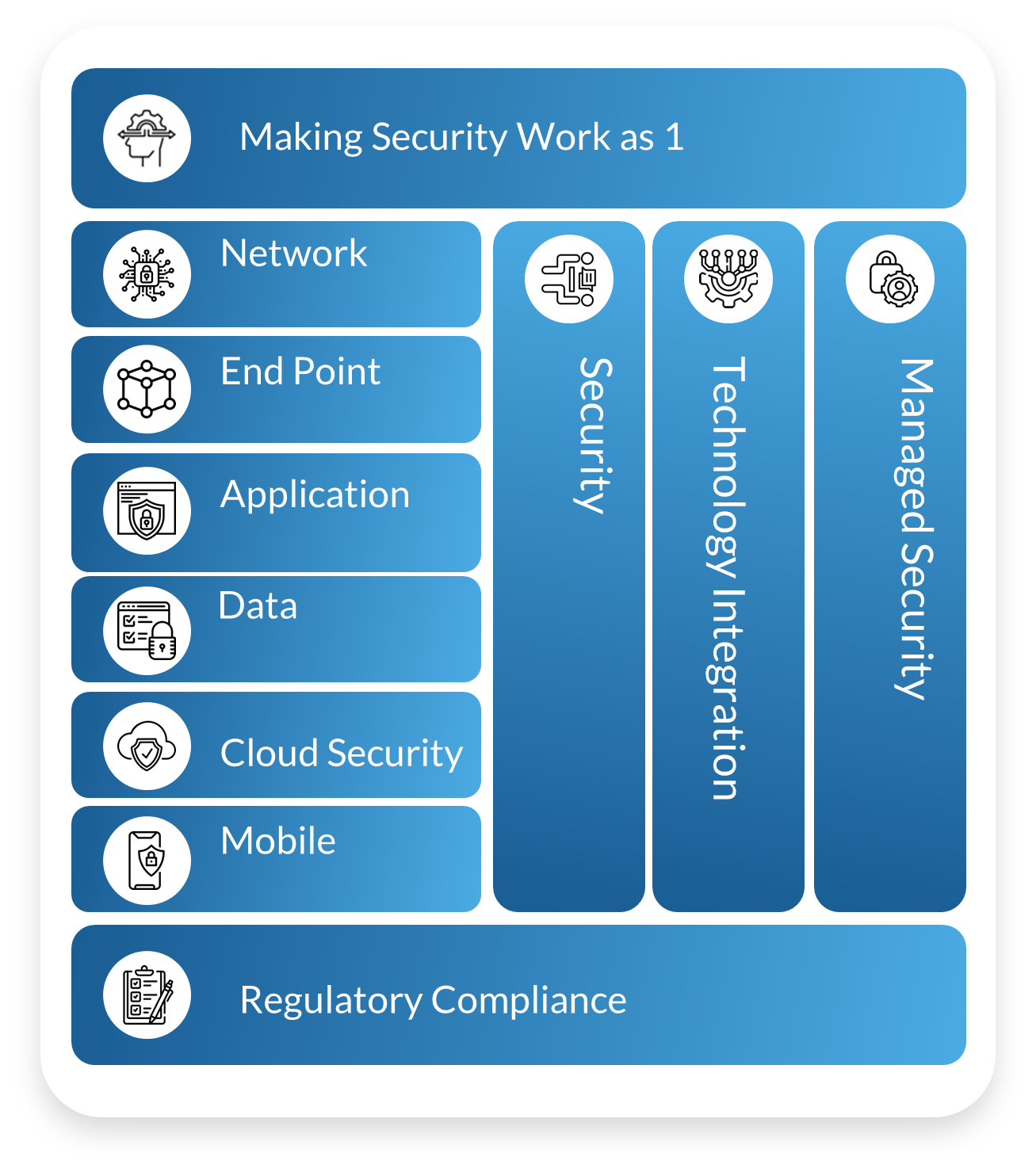
We support you through Proof-of-concept to Production via:
- Business requirements discussion
- Solution and implementation design
- Product environment configuration and tuning
- Simplify project planning and execution.
- Installation and configuration of the security solution
- Minimize efforts and Maximise ROI.
- Improve resource optimization.
- Bring in rich experience.
Our Approach
- Avoid Rip and Replace:
We evaluate current technology solutions, pinpoint gaps, and reconfigure existing platforms to maximize ROI on investments.
- “Rules Before Tools” Approach:
If current technology is not equipped to avert the evolving threats we then create a custom security architecture that meets your business needs, leveraging technology designs that align with cybersecurity frameworks like NIST-CSF, providing deep visibility, detection, and response capabilities to defend your network against cyber threats and maintain a strong security posture.
Our Methodology
- Plan and Design:
We design and plan optimized security solutions to build a robust platform, reducing downtime, errors, and expenses for your organization.
- Deploy:
-
We understand how important it is to promptly maximize your security investments. Our team offers efficient new installations and cost-effective lifecycle upgrades to accelerate security solution deployment.
-
- Operate:
Our Long-Team Consultant service offers subject-matter experts to meet specific needs, ensuring smooth operations and enhanced security.
- Optimize:
- Our optimization services reduce exposure to emerging risks through comprehensive security assessments and tailored recommendations.
- Train:
- We prioritize your company’s unique learning needs with custom training solutions, empowering your workforce with the skills for an enhanced security posture.
